
Continuous Cyber Threat and Attack Analysis
TacitRed continuously analyzes massive amounts of global attack signals and threat intelligence sources to pinpoint active exposures, attacks, and risks of over 18 million US companies – unparalleled, on-demand findings.
- Delivers fully curated and detailed threat intelligence
- Maps and visualizes external attack surface
- Identifies and prioritizes attacked and at-imminent-risk assets
- Delivers valid evidence enabling rapid threat mitigation
- Increases security analyst proficiency and reduces 3rd party risk

Extensive Capabilities, Simplified
TacitRed automatically maps your external attack surface and monitors connections and threat activity between your digital presence, cyber adversaries, and third-party entities – curated threat intelligence to accelerate proactive remediation, impact containment, and risk assessment processes.
Cut Through the Noise, Searches, and Pivots
On-demand, curated threat intelligence - take immediate, informed and decisive actions to mitigate impactful cyber exposures and risk
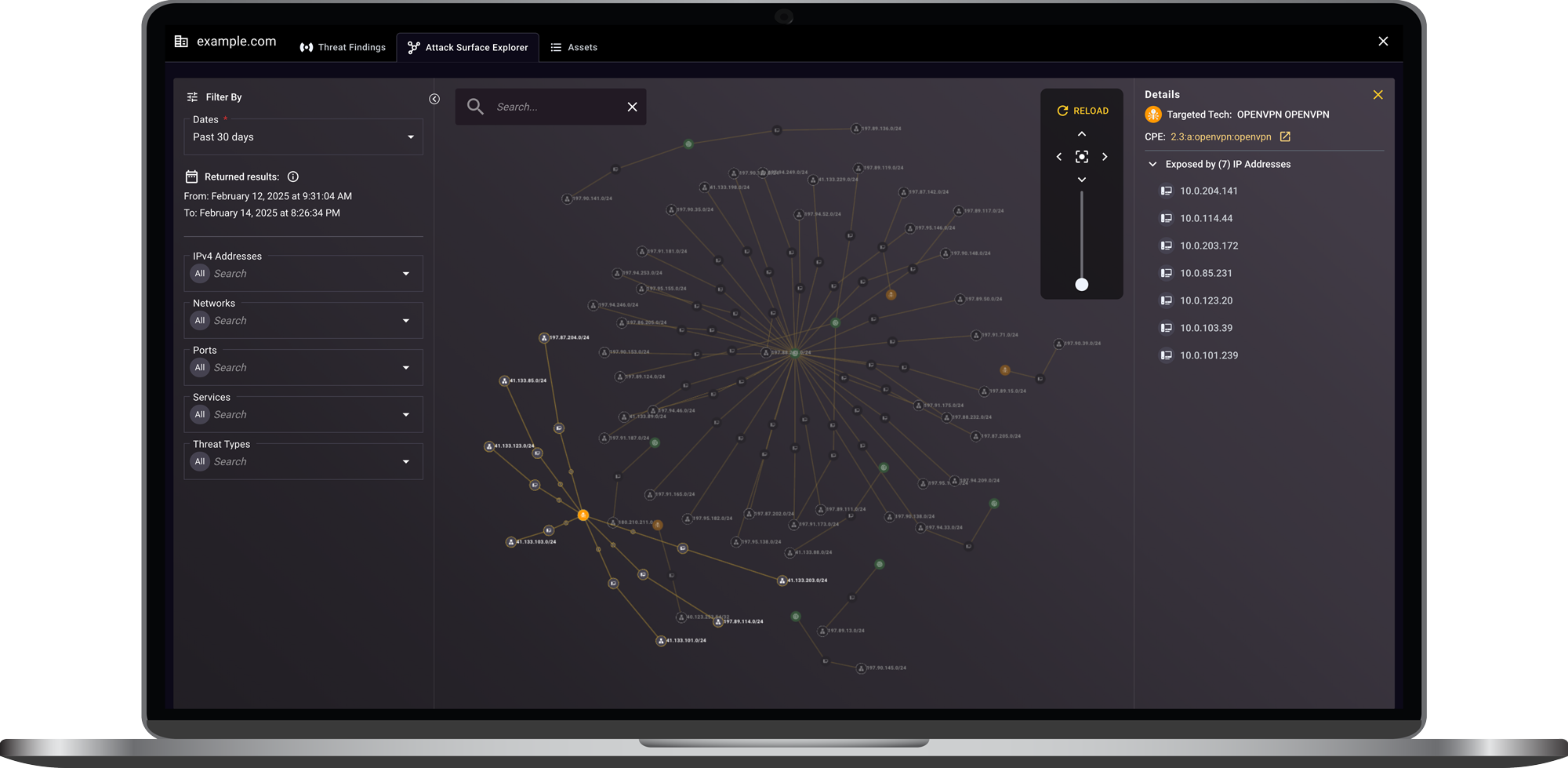

Continuous Mapping and Threat Monitoring
External attack surface mapping, visualization, and monitoring of connections and threat activity between your digital presence, threat actors, and third-party entities.
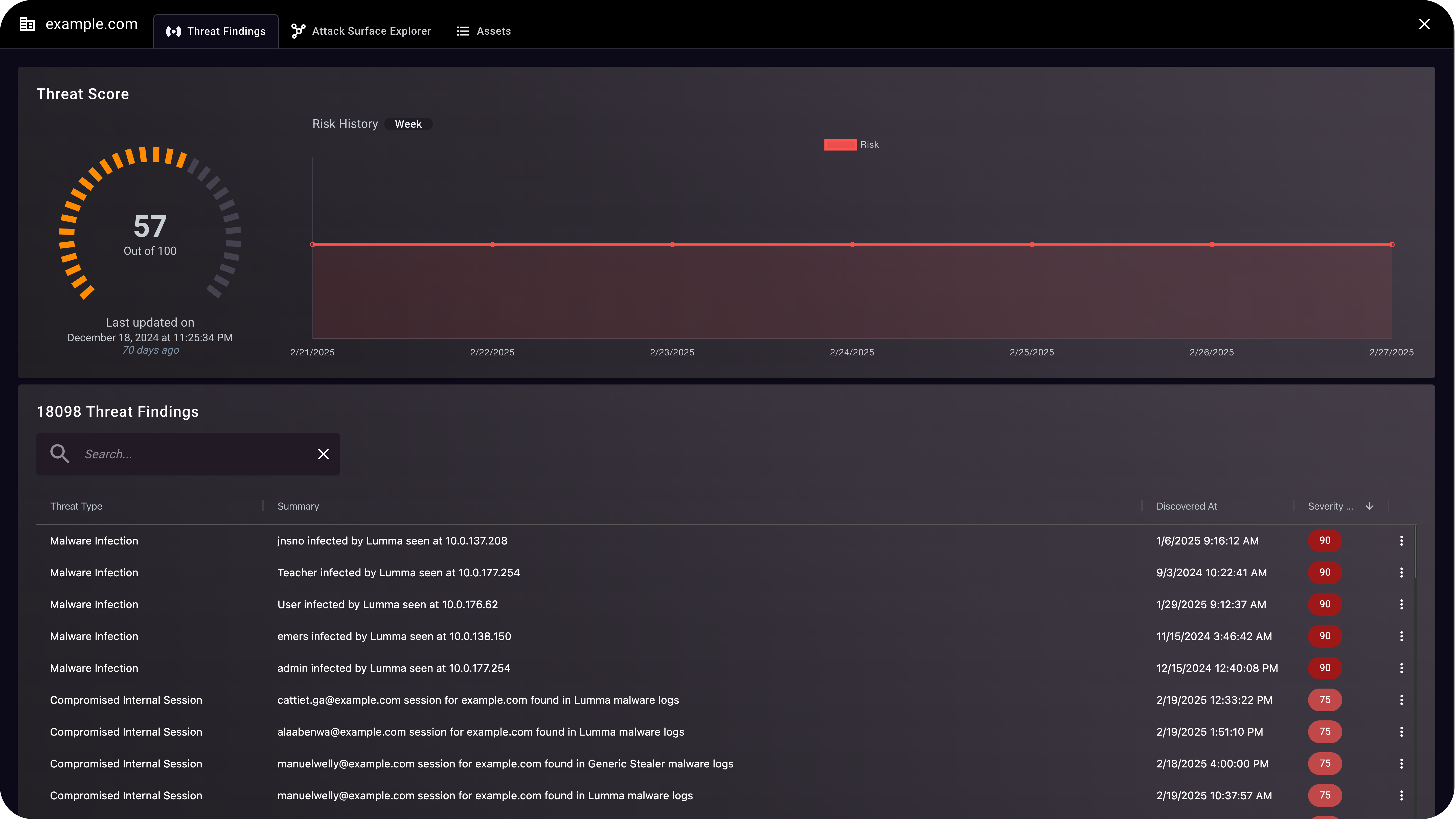
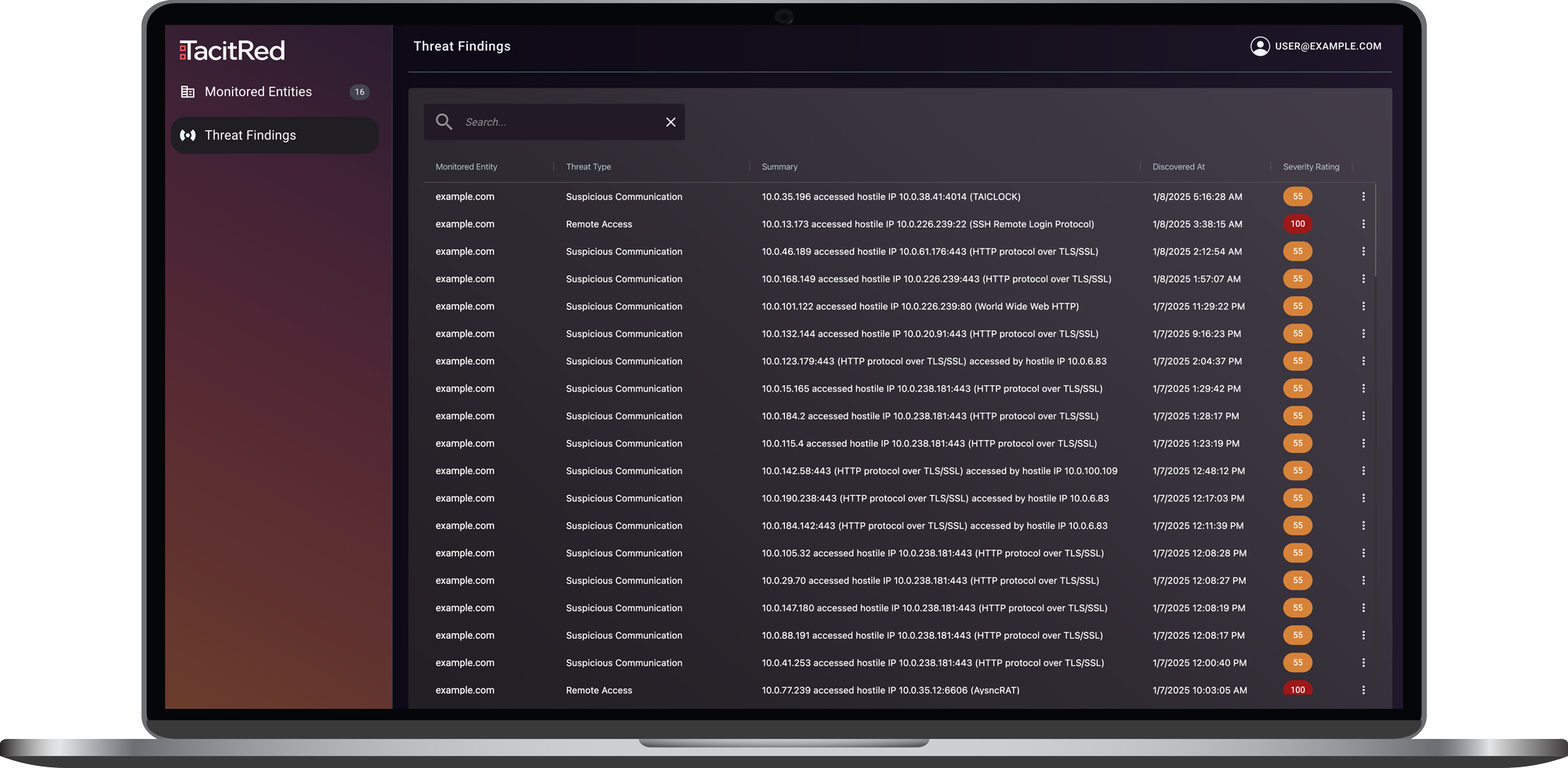
Focus Priorities On Active Exposures
Discover compromised and imminent target assets, threats, and novel attacks with attack classification, threat severity, and exposure details rather than irrelevant issues such as expired SSL certs and TLS versions.
Compromised Signal Analysis, High Fidelity Enumeration
Examine comprehensive findings categorized by threat type and cyber chain stage with full contextualization of affected machines, users, and more.
Expedite Threat Mitigation
Readily share exposure evidence with internal IR and third-party entities to streamline investigation, containment, resolution, and prevention processes.


Why Choose TacitRed
TacitRed delivers rapid time to value by combining out-of-the-box threat intelligence, attack surface management, and third-party risk reduction. Our customers realized significantly improved:
internet-facing asset inventory
and risk assessment accuracy
threat identification, investigation,
and prioritization process
threat context depth and
faster cyber threat response
user feedback as of April 2023
Value for Cyber Security Professionals