
Product
Challenge
Security teams need fast, effective response to counter cyber adversaries exploiting employees, suppliers, and internet-facing assets. Unfortunately, analysts have limited attack surface visibility and are inundated with potential exposures, alerts, and threat intelligence noise – exerting effort on often outdated, inaccurate, incomplete, or irrelevant findings that impedes mitigation.
Increase in external
attack surface incidents1
employing stolen credentials, phishing,
and asset exploitation techniques
Nominal attack surface threat
intelligence tool effectiveness1
due to threat data varying in relevance or
substantiation - mostly used to enrich
investigation after issue discovery
External Attack surface programs
still in early stages of maturity1
with only semi-structured processes
and reactive protection mechanisms
Solution
TacitRed delivers continuously curated, prioritized, and detailed attack surface intelligence at machine speed — analysts can focus on compromised and at-imminent-risk assets with interactive visualizations and comprehensive threat scoring, insight, and contextualization. As a result, organizations optimize resources, mitigate data breach exposure, proactively improve their security posture, and help reduce third-party risks.
“Amazed by the depth and speed of the curated intelligence. I was able to see a good number of unaccounted assets and serious issues that our existing tools missed. Prioritization and threat detail saves a lot of manual work.”
Lead Security and Threat Analyst
Insurance Company

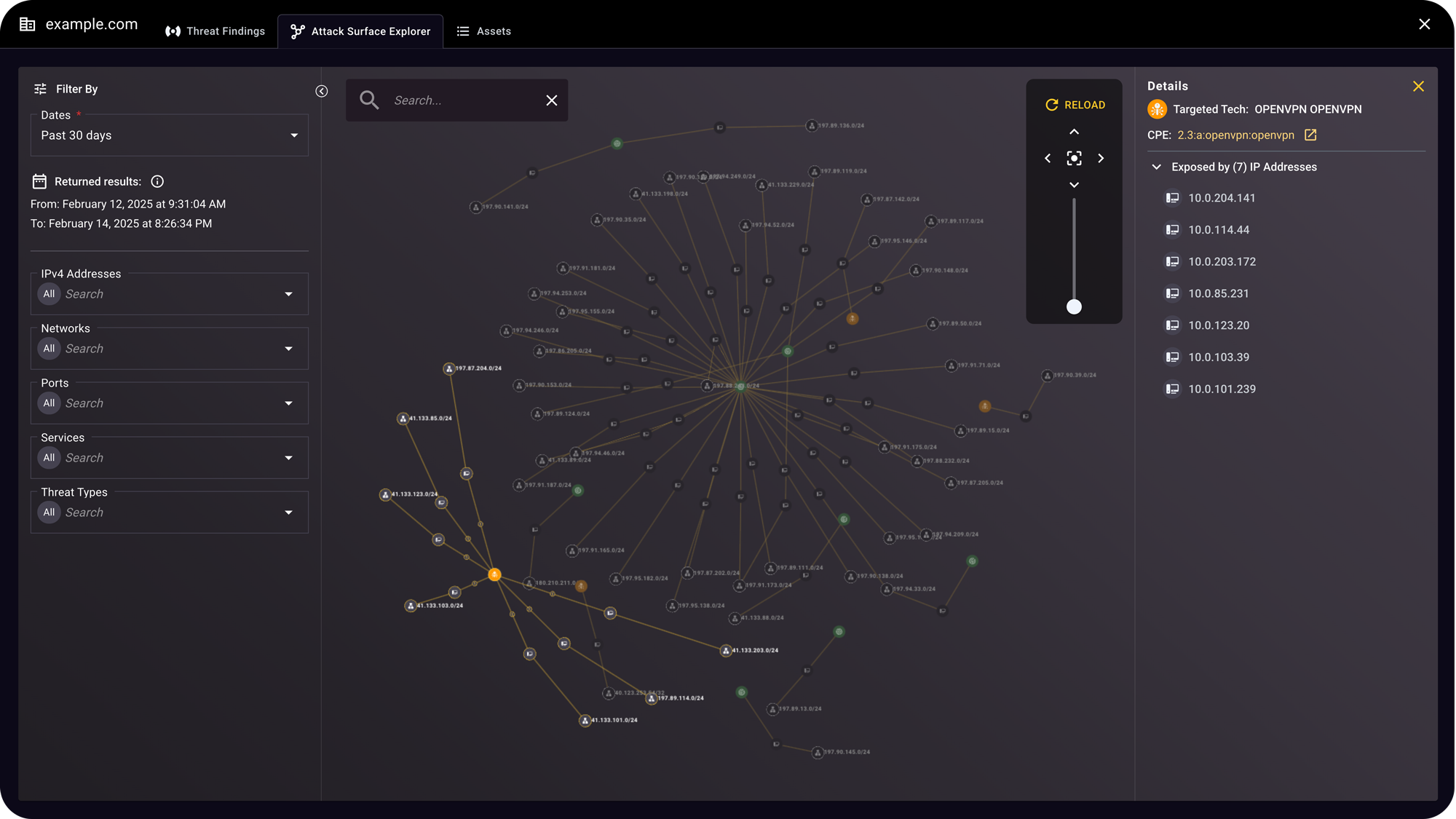
Continuously analyzes and maps your internet-facing assets, while dynamically monitoring the connections and threat activity between your digital presence, threat actors, and third party entities.
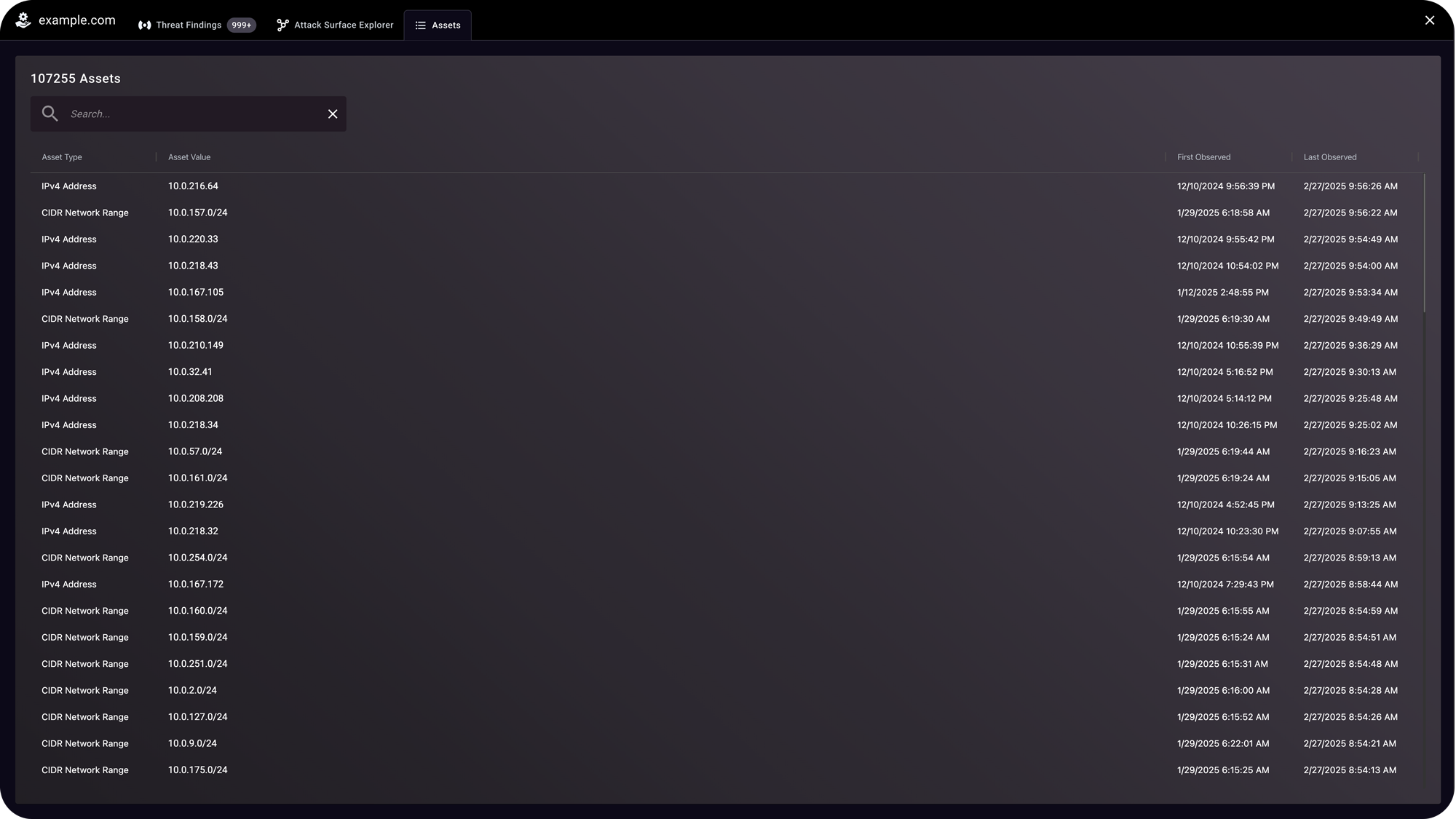
Understand the overall security posture of your external attack surface. The interactive, searchable, and filterable Attack Surface Explorer provides visualization of IP addresses, exposed attack surface and targeted technology findings, and key exposure details.

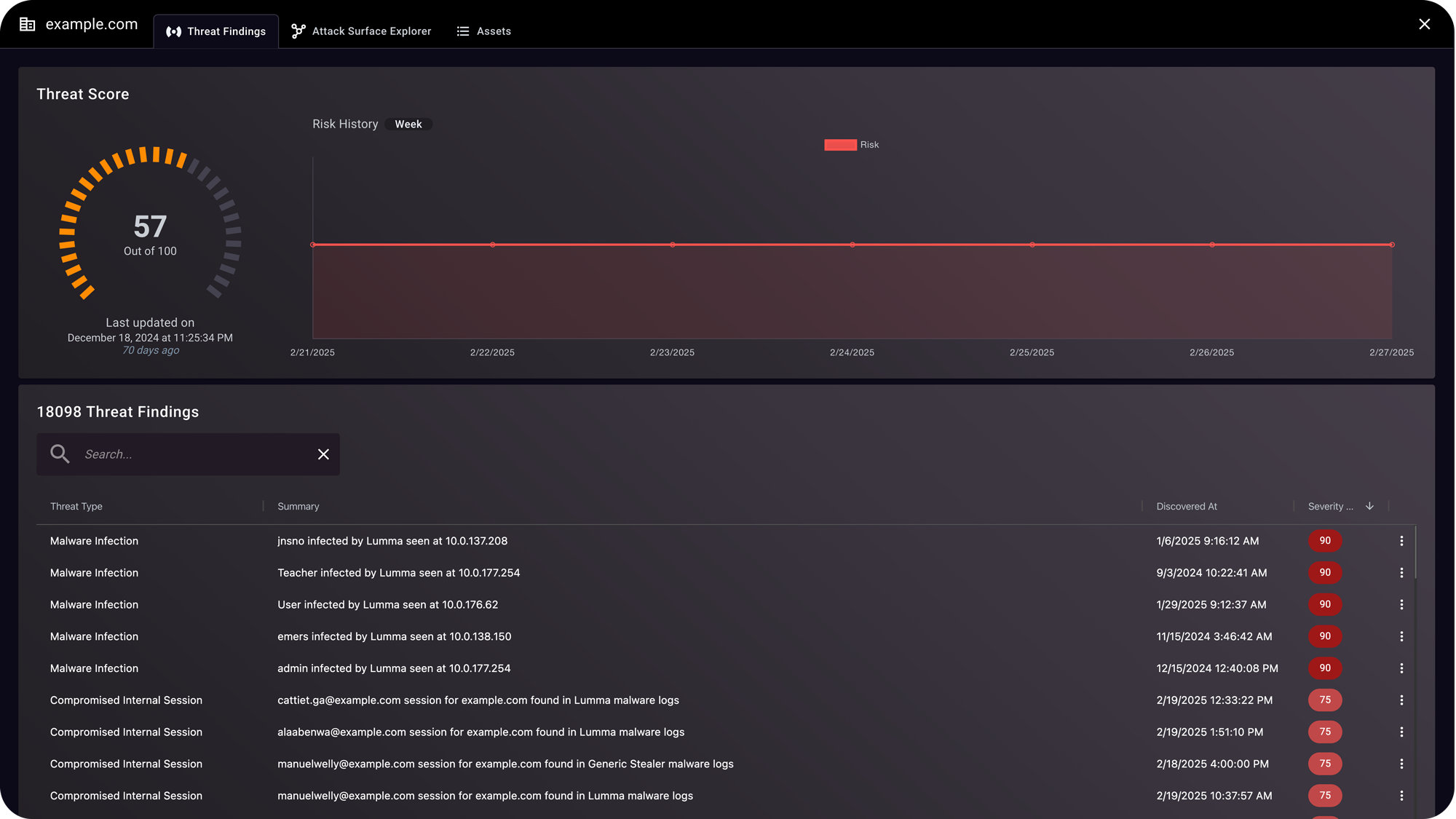

Leveraging advanced, curated threat intelligence to readily examine compromised and high target assets with full contextual details prioritized by severity. Investigate valid security exposures with high fidelity.
Expedite mitigation efforts by sharing curated findings with incident response teams inclusive of asset severity rating and detailed exposure evidence. Enrich threat intelligence within your SIEM, SOAR, SOC, and service management systems via API integration.
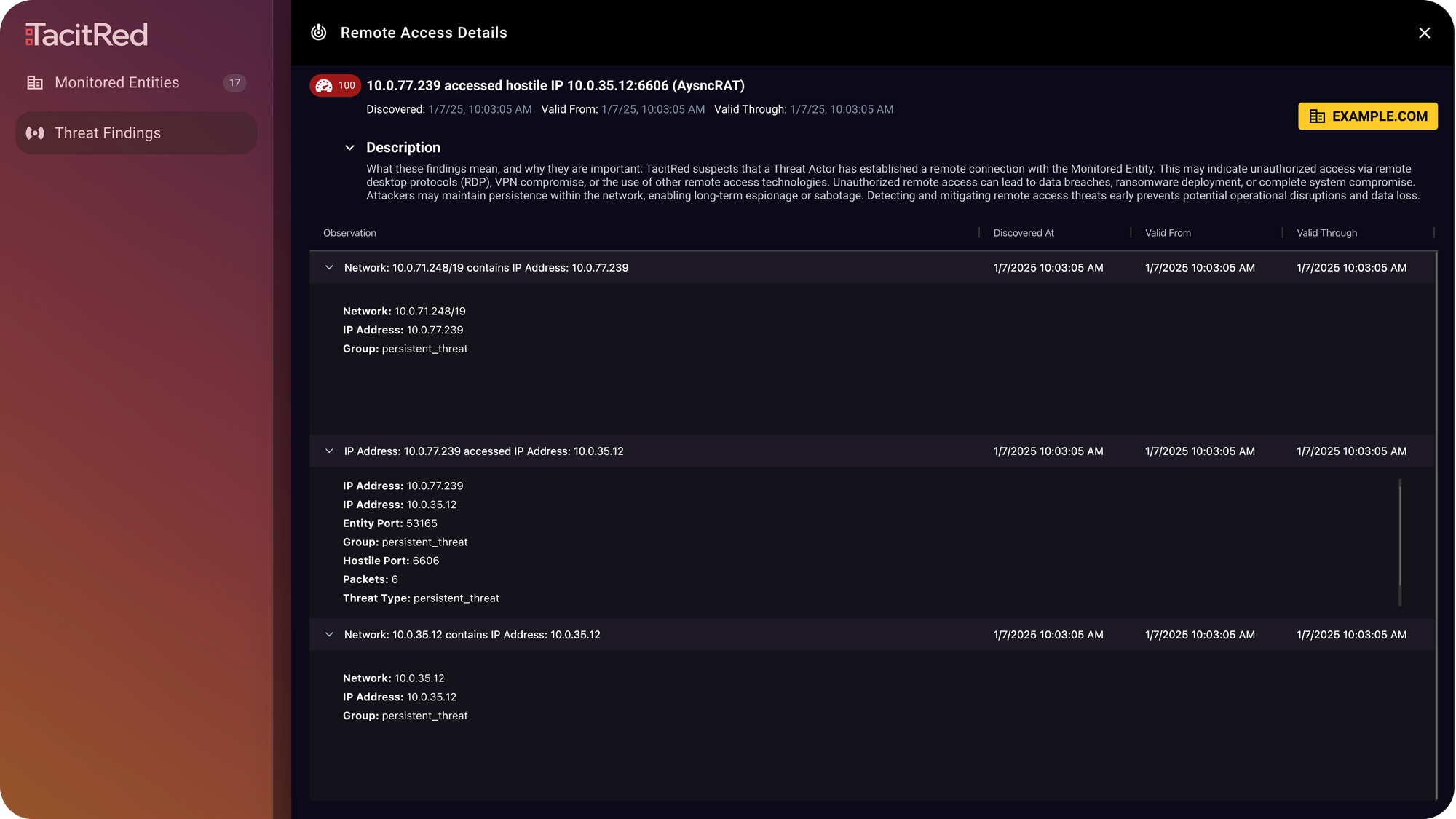

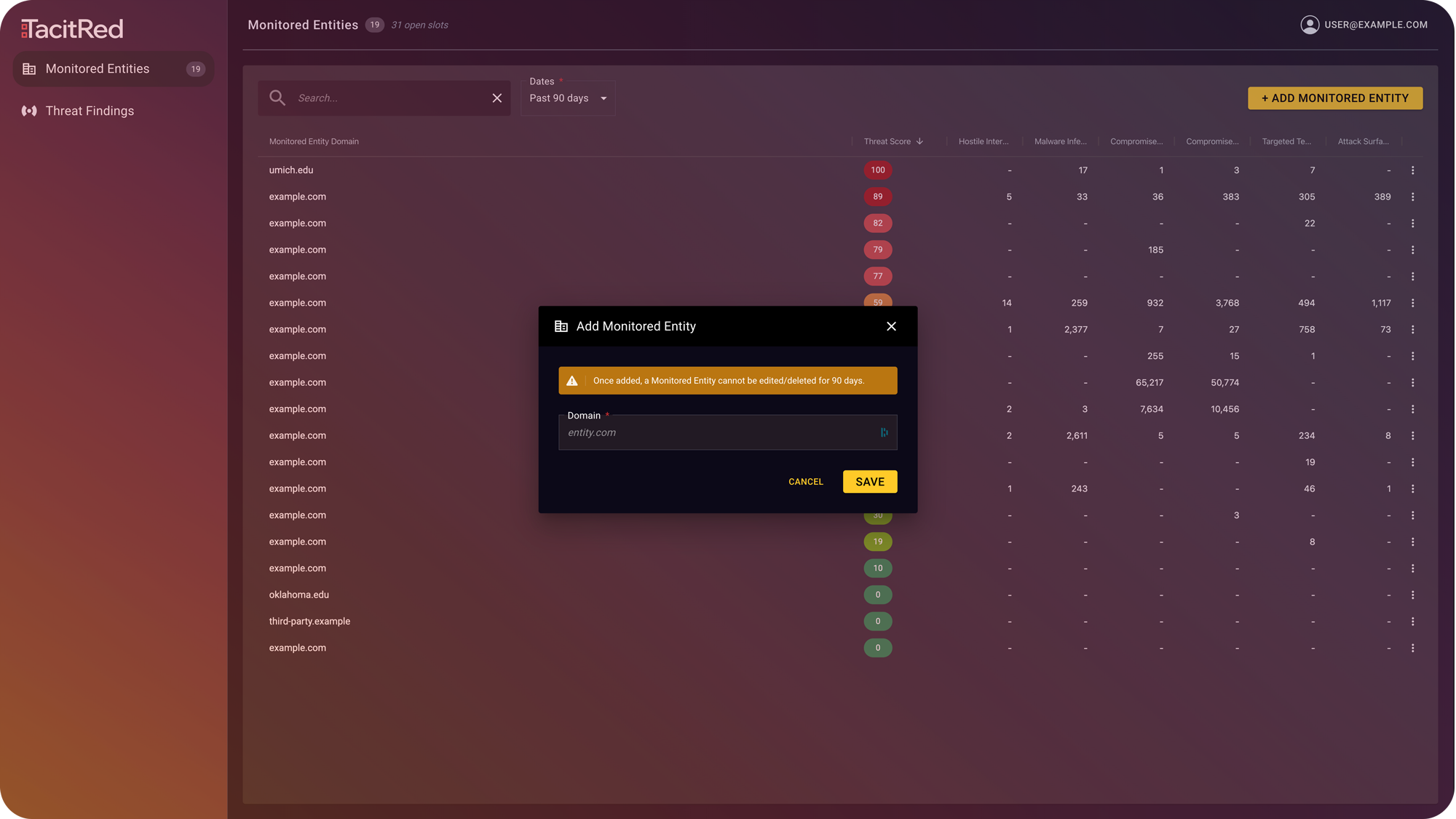

Assess your extended attack surface by entering the domain of the third-party entities you do business with, such as subsidiaries, partners, suppliers, agents, and service providers. Share the transparent threat score and crucial findings to facilitate their corrective actions.
Inner Workings
TacitRed delivers on-demand Tactical Attack Surface Intelligence covering 18 million US companies. Offered as a turnkey SaaS solution, TacitRed continuously analyzes massive streams of internet traffic and attack signals, and a broad array of threat intelligence sources through its patented Hierarchical Complex Event Processing (HCEP) engine to achieve global attack surface asset-to-entity associations, threat actor activity monitoring, threat visualization, and comprehensive exposure and exploitation context.
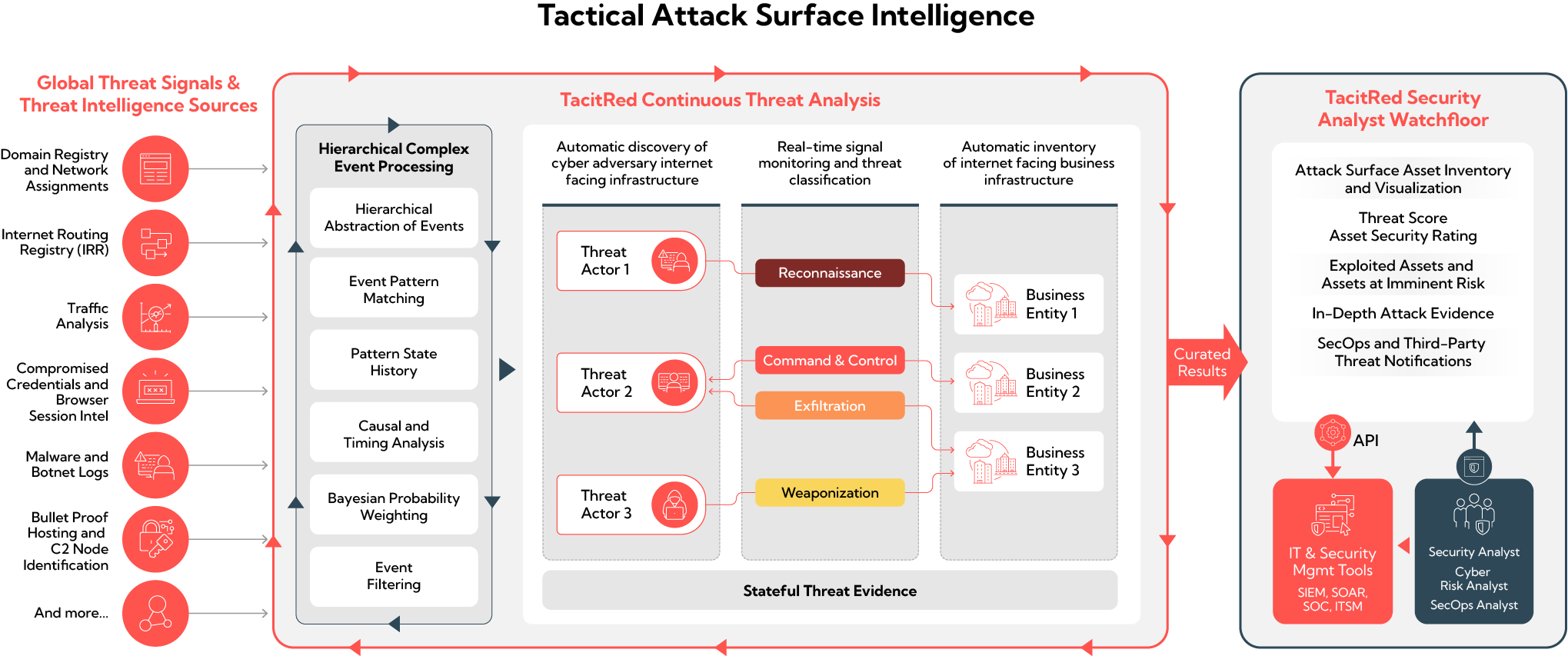


Curated Threat and Attack Analysis
TacitRed dynamically monitors attackers, your organization, and the entities you do business with – providing findings that reveal high-severity attack surface security issues to resolve and prevent with detailed evidence.
Instant Findings
Applies our patented complex event processing platform to constantly correlate threat patterns to deliver curated intelligence on demand.
Timely Threat Intelligence
Autonomously processes massive amounts of threat data from aggregated sources 24/7 to provide current and curated intelligence.
Dynamic, Accurate Scoring
Threat scoring is based on real security issues, with detailed root cause—threat and risk analysts avoid wasting time on spurious findings.
Actionable Intelligence
TacitRed is designed with the threat responder in mind, purposely tuned to deliver the most actionable findings—not more noise.
Comprehensive Context
Visualize and examine attack surface assets and issues prioritized by severity, categorized by threat type and cyber chain stage, and with full triage details.
Straightforward to Use
A simple, intuitive, and interactive dashboard offers analysts crucial information to make informed decisions to mitigate damage.
Massive Signals Processing
Rapidly processes billions of streamed records through our advanced, cloud-scaled analysis engine to overcome absurdly challenging datasets.
Intelligence Synthesis
Combines available industry intelligence and proprietary sources to give the best possible threat insight to respond to and prevent incidents.
Third-Party Risk Reduction
Evaluate third-party risk, such as subsidiaries, agents, and suppliers, and share actionable results with as much detail as your first-party risk.
1 2024 Attack Surface Threat Intelligence report by Cybersecurity Insiders (Oct-24)