This blog is a continuation of Part 1, which you can find here.
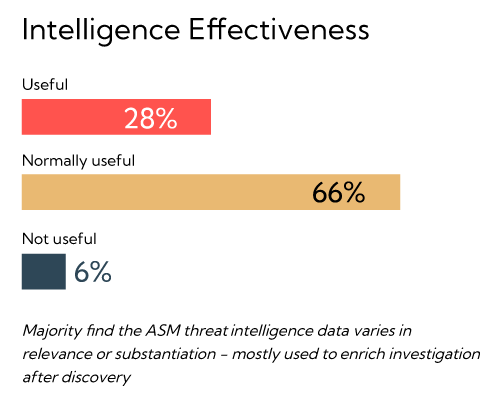 The survey further assessed how professionals would rate the usefulness of their organization’s attack surface management and threat intelligence tools. The findings pointed to an overall negative outlook. On the effectiveness of current attack surface intelligence tools, only a small portion of organizations are realizing the full value from the tool’s capabilities. While 28 percent of respondents rate their tools as useful, the majority (66 percent) found their tools only nominally useful.
The survey further assessed how professionals would rate the usefulness of their organization’s attack surface management and threat intelligence tools. The findings pointed to an overall negative outlook. On the effectiveness of current attack surface intelligence tools, only a small portion of organizations are realizing the full value from the tool’s capabilities. While 28 percent of respondents rate their tools as useful, the majority (66 percent) found their tools only nominally useful.
This suggests that some organizations are benefiting from enhanced attack surface intelligence to enable reduced investigation time and more proactive responses. But most organizations are still coping with generalized or poor intelligence. Tools that provide simple correlation of a company’s internet-facing assets, known vulnerabilities, possible attack methods, and dark web exposures still require analysts to spend time and effort to conduct significant investigative analysis and make further inferences with regards to active threats and prioritized actions.
The survey found that analysts are seeking more curated, pre-validated, and prioritized threat intelligence data. In addition, when survey participants were asked “what are their most useful attack surface threat intelligence sources,” 65 percent of respondents preferred broader, curated, and prioritized threat data. This is not merely aggregated or comprehensive threat intelligence, but multi-source, correlated threat intelligence that is validated, pertinent and actionable — enabling security teams to focus on the most critical threats and exposures that include the context necessary to expedite mitigation efforts. This greatly reduces the burden on security teams to identify, triage, and respond to active exposures — reducing investigation effort and increasing response efficacy.
Panel Perspective: Ross Warren
One of the trickier parts about external attack surface management is understanding what really matters. In many cases, obtaining the actual intake of relevant data for a specific company and their network infrastructure is a very piecemeal process — and starting to mature in the cyber insurance industry. Once you have the target infrastructure, assembling tools and reviewing findings can overwhelm risk analysts with a lot of noise. This can be in the form of false positives and incorrect infrastructure, which causes frustration and confusion. It is not uncommon to have to re-examine identified threats which may be incorrect or outdated. Incorrect threat data frustrates the customer as risk assessors are making an intense decision — this also harms an insurer’s reputation. Many tools will identify a long list of threat information claiming that an asset vulnerability or an open port is generating an exposure signal. In many cases, the information is old and the insured has already managed the issue — or would consider the issue insignificant. This makes for a wearisome conversation between the cyber risk insurance analyst and the client. As such, attack surface threat intelligence accuracy, timeliness, and supporting evidence are key for both the insurer and the insured.
Panel Perspective: Thomas Johnson
There is a difference between threat data and threat intelligence — and that difference is how actionable is the information. Many incumbent threat intelligence and third-party risk providers provide plenty of security issues that security teams “need to take care of”. Unfortunately, the systems make inferences based on partial details. As a result, threat scores are inaccurate and there is a lack of prioritization. A well-known example is an invalid certificate on a web service being a high vulnerability rating. But his is not the whole picture, as this type of web server exposure is insignificant.
Attack surface threat intelligence needs to lead to positive defensive outcomes — explaining the why and providing the evidence to take action. In most cases — this is missing. However, if a threat actor has compromised an account or compromised an internet-facing asset, and this results in compromised machine on the internal network — this needs to be a higher priority and explained clearly with vectors, threat type, machines, and attack stage details — so analysts can take a more rapid, prioritized and informed response.
For example, the existence of a vulnerability could lead to a negative outcome — and there are ways to mitigate this. Different security mechanisms can protect against exploiting an open RDP port. This exposed, unmanaged port will still put the enterprise on the radar of threat actors. Furthermore, that exposed port may have a weak password that can be opened as an exfiltration mechanism. Therefore, not all RDP use is the same and EASM solutions need to be able to rate and explain the risk comprehensively.
Panel Perspective: Ken Pfeil
Proactive posture management is top of mind for many CISOs. To make headway, organizations require comprehensive visibility as well as continuous exposure management. To optimize resources, this requires attack surface management and threat intelligence tooling that facilitate issue identification, prioritization, and effective response. Unfortunately, the majority of organizations still operate traditional vulnerability management programs which winds up being reactive. Risk classification processes are key to enable more effective threat response prioritization and where to focus proactive remediation efforts. Another consideration is the means to collaborate and coordinate workflows across teams, especially as larger organizations manage disparate systems. Being able to take advantage of external attack surface intelligence tools still comes down to available budget and resource allocation.
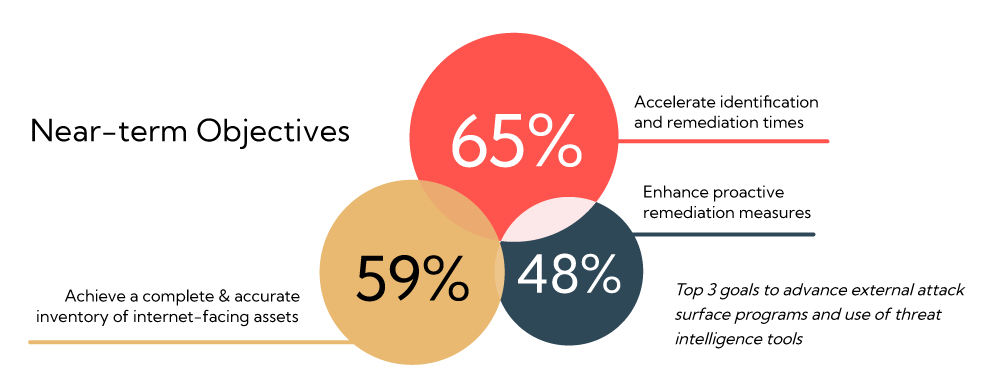
The survey asked participants about their near term objectives for advancing external attack service management programs and use of threat intelligence tools. A top priority for 65 percent of respondents is to accelerate the identification and remediation speeds of their operations. Organizations are dealing with more sophisticated and dangerous threats against an increasingly dispersed and vulnerable digital landscape. There is industry recognition of the increased likelihood of security issues and the need for faster incident responses.
Additionally, 59 percent seek to achieve a more complete and accurate inventory of all internet facing assets, which underscores the risk associated with attack surface dynamics as previously expressed in this research. Enhancing proactive remediation is a top goal for 48 percent of respondents. Highlighting the desired objective to move from reactive defenses to preventative measures that can stop threats before they can escalate. This aligns well with Continuous Threat Exposure Management initiatives that are underway in many organizations.
Similarly, 44 percent. of survey respondents of organizations are focused on enriching threat intelligence capabilities of their existing tools such as SIEM, XDR, SOAR tools — seeking to blend internal with external attack surface intelligence. This not only enhances security posture management and risk assessment processes but can serve to help automate remediation and containment actions — depending on the extent of the security exposure and business impact. Finally, 30 percent aim to reduce the volume and noise of threat intelligence data, emphasizing that while more data is being gathered, filtering out irrelevant and outdated information remains a critical challenge for security teams.
Panel Perspective: David Monahan
When it comes a proactive security posture, achieving an accurate inventory still falls back to a foundational principle of strong asset management practices and robust procedures. As with any endeavor, it is very important to engage your subject matter experts in attack surface management processes and tool selection. Without the proper inputs, an understanding of how different tools work, and how well aligned the tools will be applied to support the SME’s job — implementation and achieving objectives will ineffective.
Avoid buying a tool and then modifying your processes around the tool unless you’ve identified a flaw in the process, or have identified capability and operational gaps with your current tool which impacts your resource and coverage capacity for external attack surface management. Merely amassing tools can have the negative impact of churning your processes in addition to increasing maintenance and training overhead. Another negative outcome is competing data from different sources can impact the integrity of the tools. That does not dismiss considering new EASM and related tools — at some point, business requirements, infrastructure, and security exposures evolve where defenses need to be augmented and tools need to be replaced.
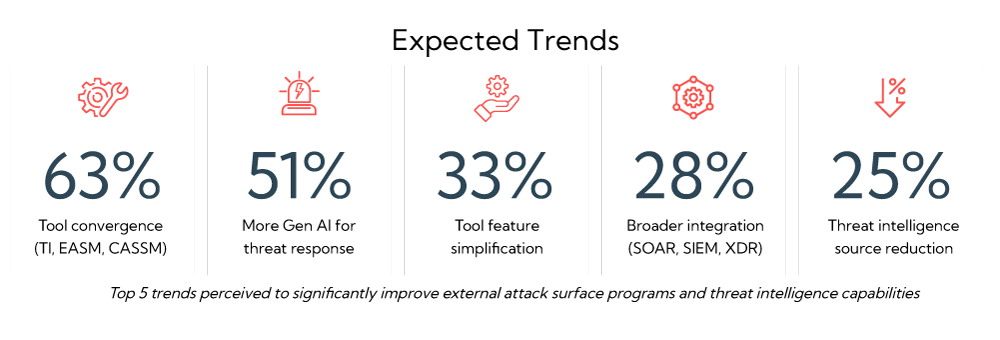
The survey touched upon perceived trends and value concerning EASM and threat intelligence. The top perceived trend, at 63 percent, was centered on the convergence of vulnerability assessment, attack service management, and threat intelligence. This conversion appears to reflect the industry’s shift toward continuous threat exposure management (CTEM). CTEM focuses on advancing processes and supporting tools to enable security teams to continuously identify and monitor infrastructure and applications, facilitate proactive remediation, coordinate greater incident response efficiency, and improve resiliency across all layers of an organization’s internal and external attack service.
Half of the survey respondents anticipate greater reliance on the application of generative artificial intelligence (AI) to facilitate threat noise reduction, validation, management, response, and mitigation. Respondents expressed improvements in tool usability, at 33 percent, and broader integration capabilities, at 28 percent, to enhance their SecOps team’s ability to improve their cybersecurity posture.
Panel Perspective: Ken Pfeil
With anticipated security tool convergence, key areas that will be of increasing need will be greater tool usability and integration. Talent is limited and the ability to ramp security operations personnel and cross-train has an impact on program success. Usability plays a great part in helping to maintain and improve productivity as well as to enrich jobs and minimize burn out. Any means for tools to enrich each other and provide greater operational insight for security teams is always positive. This is very true where automation can handle the more mundane and operationally easier actions — those that do not have the potential for operational detriment. EASM tools need to continue to improve usability and integration features. The other key trend that is clear is the use of Generative AI. The application of Gen AI within security tools, including EASM, appears to be progressing significantly. Gen AI has already provided value in noise reduction and identifying anomalies. Regardless of being a new tool, organizations are not going to throw
out their investments for any particular tool. Tools do need to fit processes and cost-effectively advance
defense capabilities.
Panel Perspective: Thomas Johnson
Artificial Intelligence appears to be able to support security analysts in many ways. The ability to have a richer, interactive user experience and greater operational efficiencies it clearly a win win. It is all about improving speed, accuracy, and capacity. EASM not only continously assesses an enterprise’s internet-exposed resources, but also extends to the supply chain of an entity. Any means for AI to progress connecting the dots and improving operational scalability when it comes to being more responsive to supply chain risks will make a great difference. AI applied to improving the user experience is going to make EASM tools more approachable — not only for technical security analysts but perhaps for non-technical business leaders.
Panel Perspective: David Monahan
Artificial Intelligence is going to make a significant positive impact as it touches many improvements for security operations and the tools they use; inclusive of attack surface threat intelligence. AI is excellent at reducing threat noise and finding security issues and anomalies — finding the diamonds out of the coal and producing valid targets for the analyst. AI also improves usability and it can support threat analyses and by correlating information from different sources. And it also can be used to support convergence or integration as it can ascertain what data to share with specific tools to trigger faster responses. That being said, there are various levels of AI, and in some cases, we need to consider potential risks — such as bias and traceability issues, that might inaccurately alter results and result in unwanted actions. We want to avoid a “Skynet” scenario. Ultimately, the goal is to ensure that AI enables security personnel to have a much better user experience and to be able to operate and collaborate more efficiently.
Heading into a positive direction, investments in attack surface threat intelligence tools and programs appear to be on the rise. The survey asked respondents to assess the extent of budget for external attack surface management tools and threat intelligences to change for 2025. 90 percent of respondents expect budget increase for 2025, and of these, 40 percent anticipate significant increases of more than 20 percent. This reflects the growing recognition of EASM’s importance in mitigating risks and securing their enterprises growing attack surface.
Compiled by Scott Gordon.
Scott Gordon is the CMO at Cogility Software. An avid cyber evangelist, he brings more than 20 years of experience contributing to successful early and late-stage enterprise software and SaaS start-ups. Prior to Cogility TacitRed, he held executive leadership positions at Pulse Secure, ForeScout, RiskIQ, AccelOps, and Protego. Scott holds a CISSP security certification.
Read the full report "2024 State of Attack Surface Threat Intelligence", conducted by Cybersecurity Insiders.
Watch the recorded webinar.
Read our executive deep dive.