Even with today’s modern external attack surface management (EASM) tools, investigating threat findings has remained a tedious task.
Cyber security analysts are more akin to wilderness explorers as they navigate forests of windows, mountains of tabs, and oceans of spreadsheets. All day…. copy, paste, copy, paste, search…. again, and again and again and again across different threat intelligence sources to triangulate, validate, and prioritize attack surface security issues. While some EASM tools attempt to provide our explorers a map from which to navigate, analysts can still find themselves repeatedly running into dead-ends or unable to efficiently course-correct to their destination within the cyber maze they contend with.
Conventional attack surface management tools often flood security teams with extraneous threat intelligence, false positives and “highly critical” expired SSL certs and TLS versions. TacitRed’s tactical attack surface intelligence already empowers analysts to focus on the active exposures and imminent threats with full evidence across an organization's external attack surface. And now TacitRed has introduced a new Attack Surface Explorer feature - the "map" for cyber security analysts. Check out this teaser video.
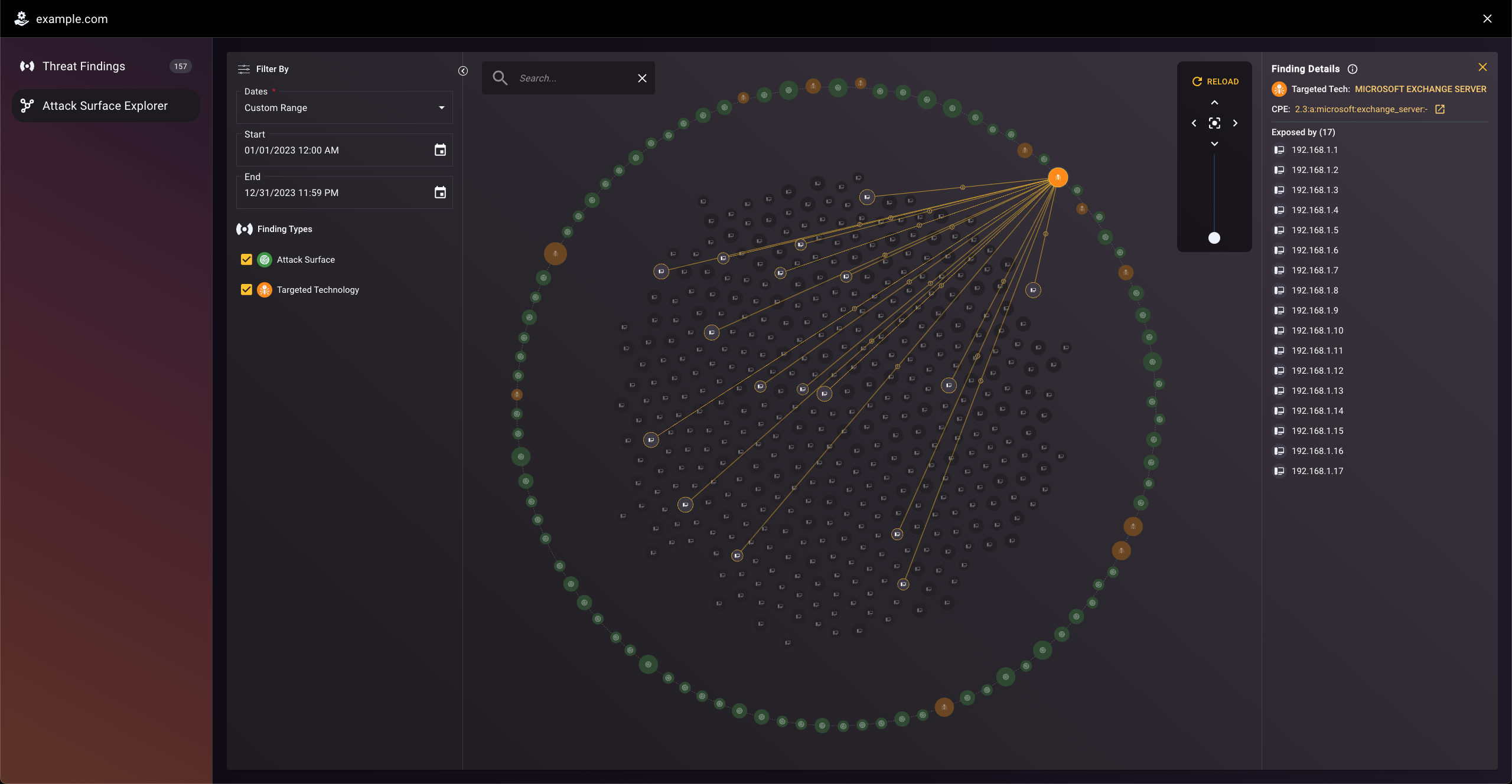
The new Attack Surface Explorer feature enables analysts to easily see their attack surface, understand threat vectors relationships, jumpstart investigations and expedite mitigation. It provides a rich and fully interactive visualization of the attack surface and technology findings that TacitRed has enumerated for a given monitored entity (domain) and time range.
- Every uniquely identified CPE and IP address is displayed as individual nodes within the visualization
- Attack Surface and targeted technology nodes are color coded for easy identification
- Node sizes scale in size to indicate the total number of exposures and attack associations to help draw attention to potentially problematic IP addresses, or CPEs
- Users can select nodes to dynamically see the relationships between the identified IP addresses and the services (CPEs) that they expose (and vise-versa)
- Users can hover over nodes to quickly get a glimpse of its characteristics - either its IP address or CPE - to help speed up investigation.
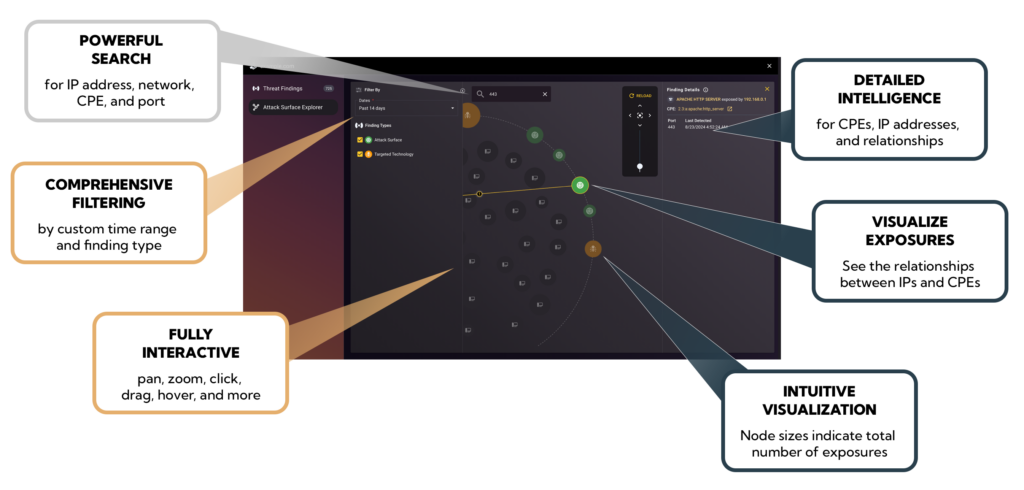
- Users can pan, zoom, and even drag and drop nodes to get the optimal view during an investigation
In addition, the robust visualization the Attack Surface Explorer has additional capabilities that greatly help cyber security analyst’s investigation efforts:
- Comprehensive filters enable Cyber Security Analysts to focus their investigation onto specific time windows and/or findings of interest.
- A powerful search bar allows analysts to search on nearly every facet of the findings within the selected time range: IP Address, CPE (full string or even individual attributes), IP Address Ranges and even Ports used.
- Drill into details right within the visualization – gain attributes on the specific IP Addresses exposing services (CPEs), the port used for communication, the last detected time for any CPE - IP relationship, and more
Beyond that, the Attack Surface Explorer feature fully leverages TacitRed’s active attack and imminent threat findings:
- Persistent Threat Findings: Analysts can quickly identify the specific services that have communicated with threat actors by searching for their Targeted Asset’s IP Address
- Malware Findings: Analysts can search by the machines IP address, or even its CIDR, to better assess the potential depth and breadth of impact
- Compromised Credential/Session Findings: Analysts can independently identify the networks/machines that have been affected they can again search the Attack Surface Explorer to better understand the potential impact of such compromises
- Reconnaissance Findings: Analysts can quickly search the networks scanned by Threat Actors to identify and patch any risky technologies that were left exposed to help prevent potential incidents or breaches.
We are absolutely thrilled to be releasing this new feature and other enhancements to our customers, but we are even more elated to be able to offer this capability and more to our Free trial users. Yes, you heard that right. During the free 30-day trial of our updated TactiRed Essentials Edition, analysts can fully use that Attack Surface Explorer feature as well as gain access to detailed intelligence for all TacitRed’s threat findings. AND - after the 30-day trail, analyst can CONTINUE TO ACTIVELY USE TacitRed and many of its features, including the Attack Surface Explorer, for FREE. All you need to get started is a business email.
Check out the latest offerings HERE. Sign up for a Free Trial of TacidRed Essentials edition HERE to get instant access to fully curated, prioritized, and actionable threat findings within your external attack surface.