
(Updated 061024) Hudson Rock prior revealed a cybercrime intelligence investigation regarding a potential Snowflake data breach, its ramifications, and details made by a dark web data broker claiming to be the threat actor. Hudson Rock recently took down their investigation content in lieu of legal notification by Snowflake.
The cybercriminal “Whitewarlock” claimed to have attempted to blackmail Snowflake to the tune of $20,000,000 in BTC to not disclose sensitive customer data stored in Snowflake. According to the threat actor, Snowflake did not pay, and the threat actor then started selling data breaches individually starting with Ticketmaster, then Santander. To gain access to this data, the threat actor claims the source was one employee from Snowflake infected with malware on their computer in October of 2023. Since then, Whitewarlock’s assertions have been heavily disputed.
Snowflake issued (May 31, 2024) its own statement regarding this data breach. The notifications provided by Snowflake indicate that the threat actor gained access to the customer credentials to demo accounts belonging to a former Snowflake employee, and that such accounts are outside Snowflake’s production or corporate systems – referencing Crowdstrike and Mandiant security experts. Snowflake has issued a warning to customers regarding indicators of compromise, echoed by the U.S. CISA, and how to take steps to prevent unauthorized access.
In general, once a threat actor has access to valid session data, and/or credentials, it is trivial for the threat actor to act on objectives--either stealing data or deploying ransomware.
Session hijacking is one technique that can bypass additional controls such as MFA; to prevent this, organizations should consider using hardware tokens, session pinning, or securing access gateways with a SASE type solution.
TacitRed identifies this exact type of threat, and we are seeing similar conditions for hundreds of thousands of companies in the US that range from large SaaS providers to defense contractors.
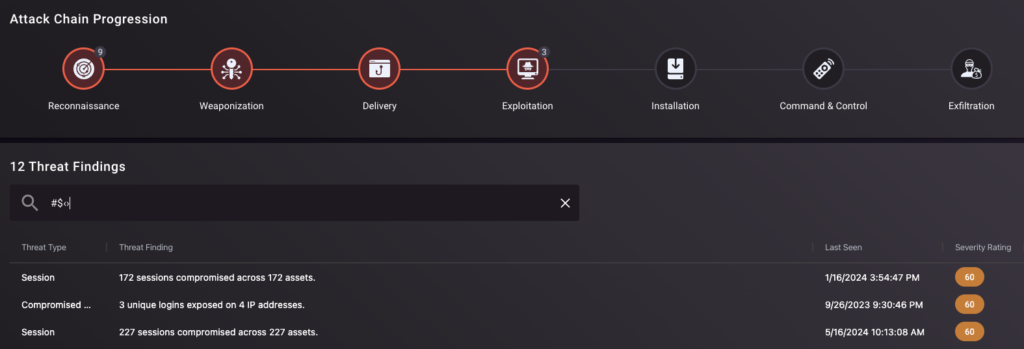
Infostealer data is a key source that we use to identify companies that have actively compromised credentials and/or sessions, as well as the malware compromises that exist within corporate networks. Our approach is to track and replicate the targeting and exploitation processes that real-world threat actors engage in.” -TacitRed