Try TacitRed for Free
No payment required. Start with just your email.
Get access to fully curated, prioritized, and actionable threat findings within your external attack surface – instantly with just your company's domain.
Pinpoint active exposures, attacks, and risks of over 18 million US companies – unparalleled, on-demand findings. See it firsthand.
Sign up today for a free 30-day trial of TacitRed Essentials Edition1 and uplevel your cyber threat analysis and response capabilities:
- Delivers fully curated and detailed threat intelligence2
- Enumerates active attack surface and calculates threat score
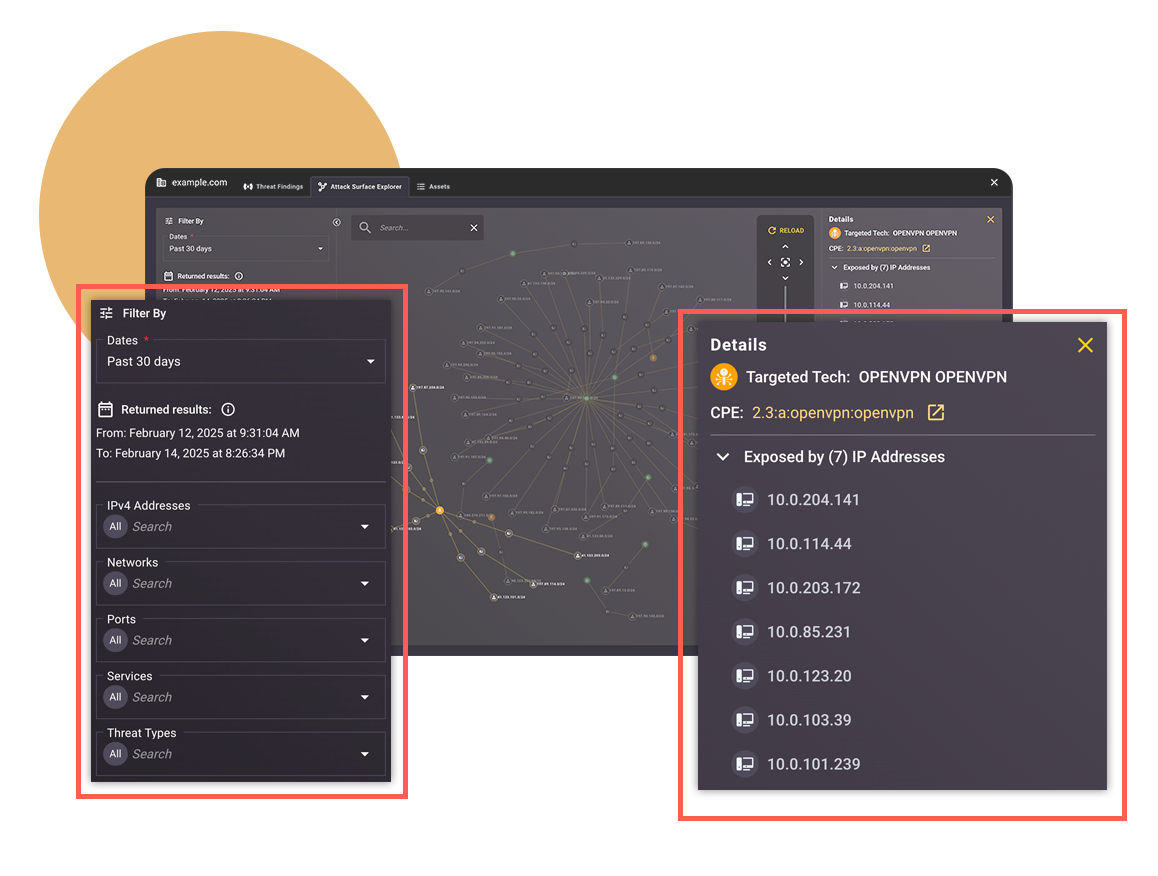
- Provides robust findings visualization using the Attack Surface Explorer
- Identifies and prioritizes attacked or at imminent risk assets
- Delivers extensive, valid evidence enabling rapid threat mitigation
Not Ready for Trial Yet? (No email required)
Note:
1 Access to select threat findings and the Attack Surface Explorer feature for up to 5 Monitored Entities is included for FREE EVEN AFTER YOUR 30-DAY TRIAL PERIOD ENDS. Visit our Pricing Page for additional Information.
2 Access to detailed threat intelligence is available during the 30-day Trial Period or within paid subscription Order term. After the 30-day Trial Period ends, certain detailed threat intelligence will be reduced to only summarized threat findings.

Take a Product Tour
TacitRed™ delivers continuously curated, prioritized, and detailed attack surface intelligence at machine speed — analysts can focus on compromised and at-imminent-risk assets with interactive visualizations and comprehensive threat scoring, insight, and contextualization.