
Pricing
Start Here
TacitRed Tactical Attack Surface Intelligence empowers security analysts to take immediate, prioritized, and decisive actions to quickly mobilize mitigation processes for attacked and high target assets. From discovery to response, it combines threat intelligence, attack surface management, and third-party risk features - putting fully curated details at your fingertips.
Choose Your Edition
TacitRed
Essentials
Ideal for:
Single security analyst to discover attack surface and monitor security posture
TacitRed
Advanced
Ideal for:
Single analyst or small security team to expand attack surface monitoring and gain additional threat details
TacitRed
Professional
Ideal for:
Single analyst to larger security team to gain full threat details and to gain API access
TacitRed
Enterprise
Ideal for:
Large organizations with expanded attack surface and third-party risks requiring special licensing
| Features | Essentials | Advanced | Professional | Enterprise |
|---|---|---|---|---|
| User License(s) Number of Users that can collaborate in the same account. | 12 | 2 | 4 | Custom |
| Monitored Entities1 3rd Party Monitored Entities are to be used for analysis/evaluation of a customer's extended attack surface (e.g. vendors/suppliers). | 52 | 20 | 50 | Custom |
| API Service REST API for integrating a customer’s threat feed into internal tools/systems. | No | No | Yes | Yes |
| Continuous Attack Surface Findings TacitRed continuously ingests and analyzes internet traffic feeds for more than 18 million US companies to provide continuous attack surface findings. | Free2 | Yes | Yes | Yes |
| Attack Surface Explorer A visual representation of a the relationship between monitored entities network(s) and their threat findings. | Free2 | Yes | Yes | Yes |
| Total Threat Score Overall risk level for a Monitored Entity given the quantity and severity of the threat findings. | Free2 | Yes | Yes | Yes |
| Findings Severity Rating Represents the seriousness of the risk presented by a given Threat Finding. | Free2 | Yes | Yes | Yes |
| Reconnaissance Findings TacitRed has identified a threat actor, or known bulletproof host scanning the monitored entity network. | Free2 | Yes | Yes | Yes |
| Targeted Technology Findings Enumerated technology known to be targeted by threat actors. | Free2 | Yes | Yes | Yes |
| Advanced Persistent Threat Findings TacitRed has identified internet traffic that suggests a Threat Actor has established a connection with the Monitored Entity. (e.g. Remote Access) | Yes3 | Yes | Yes | Yes |
| Compromised Credentials Findings Identified credentials that have been stolen directly as a result malware. This is not an aggregation of publicly disclosed data breaches and data dumps. | Yes3 | Yes | Yes | Yes |
| Compromised Sessions Findings TacitRed has evidence of threat intelligence indicators that the monitored entity has stolen session cookies on enumerated assets. | Yes3 | Yes | Yes | Yes |
| Malware Infections Findings Through analysis of adversary infrastructure and internet traffic, we have detected a high likelihood that the monitored entity has malware on enumerated assets. | Yes3 | Yes | Yes | Yes |
| Technical Support 1st Party Monitored Entities are to be used for domains/networks under control of the customer. | Online | Online | Online | Dedicated |
1 Domain names entered for Monitored Entities can be changed after a 90-day period
2 Remains free after Trial Period, however, account will be terminated after 60-days of inactive use
3 Detailed findings are only included during Trial Period or within paid subscription Order term
Available Add-ons
Users
Monitored Entities
Note: Add-Ons are available in TacitRed Advanced and Professional Editions
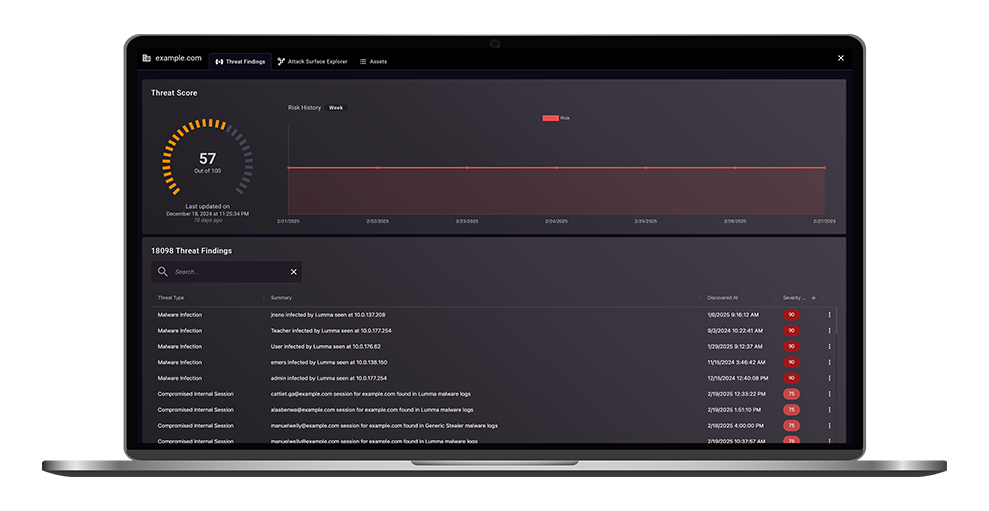

Take a Tour
Seeing is believing. Take a quick tour of TacitRed functionality. See how by just entering a domain name unlocks fully curated attack surface threat intelligence.