This is the first of many blog posts on the insights on threat actor activity that Cogility's TacitRed is finding with our unique ability to correlate terabytes of daily data across dozens of data feeds. Stay tuned as we continue to produce intelligence.
Supershell is a C2 infrastructure run on webservers to provide a user interface to facilitate remote connections, with an additional malicious toolkit. Supershell was initially published on 03/28/23 on the Github of tdragon6 in Chinese and English (https://github.com/tdragon6/Supershell/tree/main).
Supershell: A New C2 Infrastructure
One of the latest C2 frameworks to emerge in March of this year is Supershell. The C2 runs on a webserver and is described on the GitHub page it’s hosted on in the following way: “Supershell is a C2 remote control platform accessed through WEB services. By setting up a reverse SSH tunnel, a fully interactive shell can be obtained, and it supports multi-platform architecture” Payload.
Additionally, we can see the author summarize the architecture of the C2 framework in the following diagram:
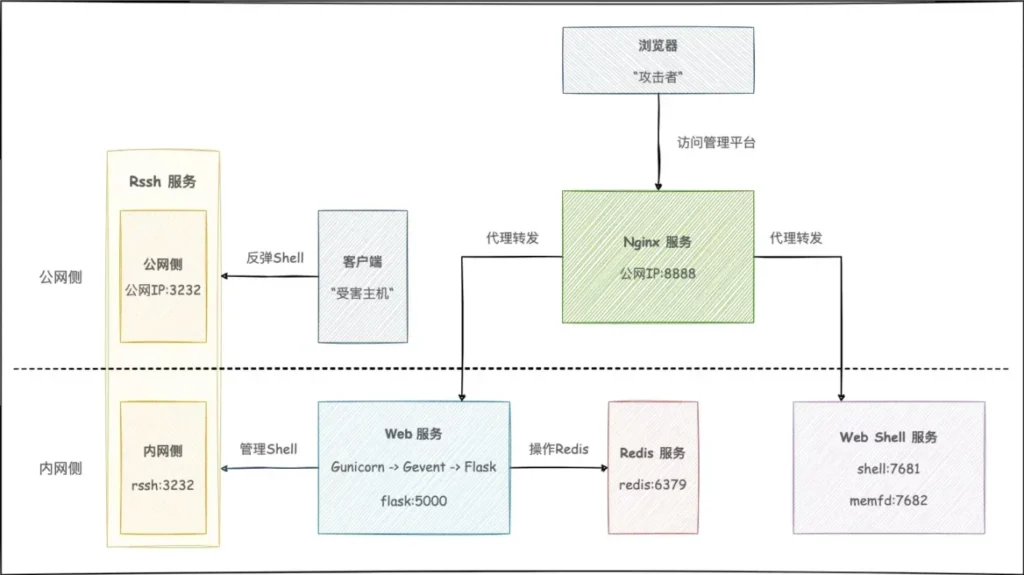
From the GitHub, Supershell supports the following features:
- Support concurrent team collaboration, use all functions in one browser
- Rebound Shell client Payload that supports multiple system architectures, integrated compression and anti-virus
- Support client disconnection automatic reconnection
- Support fully interactive shells on all platforms, support using shells in browsers, and support sharing shells
- Support back connection client list management
- Built-in file server
- Support file management
- Support memory injection, that is, the file does not land and execute Trojan horse (memory horse)
- Support Windows to install reverse Shell service and Linux to try to migrate uid and gid
With this added toolkit, it’s not much of an analytic leap to assume that this c2 will be used nefariously. Additionally, use of a GUI lowers the barrier to entry, and allows management of the server from an individual that does not know how to use a shell.
Enumerating active Supershell infrastructure:
To enumerate servers running this command and control, we can simply query internet server search engines to look for servers with responses that contain /supershell/login in the URI and “supershell” in the http response. Since this is a web-based command and control, it’s very simple to find on any sort of Shodan-type search engine for the internet.
When browsing the page, we can see several indicators to hunt this login panel.
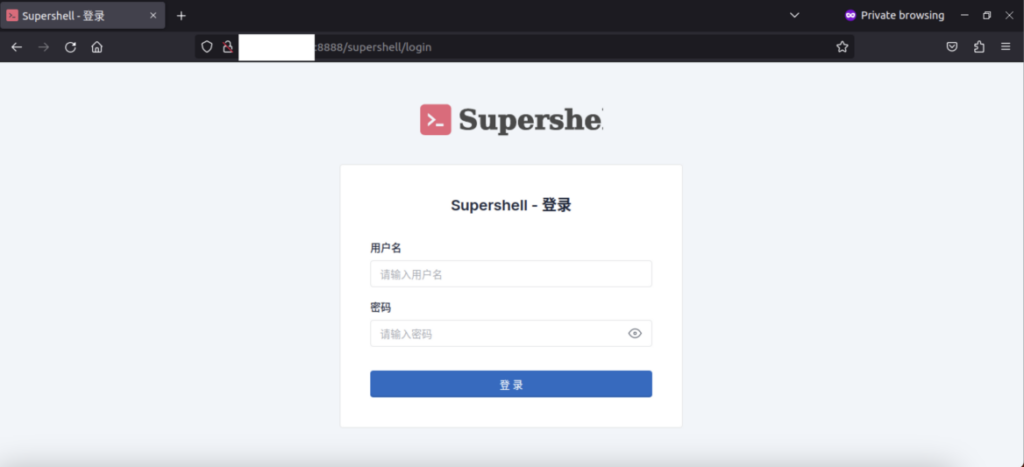
Measuring impact:
We observed about 132 Supershell servers deployed from 8/21/23-8/28/23.
To visualize our sample, we plotted a map detailing the found C2. While this isn’t an exact geographic match for the infections, we can approximate where they are geolocated by ASN. As the GitHub is written in Chinese, it is not surprising that China has the most setup C2 of our sample.
While we only presented a 30-day sample of the infrastructure here, since the C2 was posted in March we’ve seen exponential growth of active servers. This is likely because logging into a webserver is much easier for an adversary than keeping track of tons of remote shells.
As a result, companies should track this activity and build signatures for their detection systems to find any network interaction with or hosting of Supershell servers. While some servers found may be honeypots or legitimate use cases, the toolkit provided with the software can be used for nefarious ends.
TacitRed threat intelligence is giving us unprecedented insight into the growth of new malware C2 infrastructures—where they are being run, who is running them, and what impact it's having on business. With this baseline established, we'll continue to track this new threat as it develops to ensure our customers know when actions are taken against them or their suppliers.